During his short stint as an identity thief, Dan DeFilippi stole dozens of identities off the internet and pilfered more than a half a million dollars from banks, creditors, and innocent individuals.
In 2002, DeFelippi decided that buying stolen credit card data wasn’t whetting his appetite enough. Late one night, he set up a clone of PayPal, which, at the time, was in its infant stages and fresh off an IPO.
“The opening screen looked just like the real site, but it had a pop-up that told the visitor he was locked out of his account and had to re-enter all of his information,” says DeFelippi.
Within 15 minutes, he had hundreds of responses—full data sets of real individuals who’d mistakenly fallen for DeFelippi’s ploy. Using a bank identification number database and college directories, he ferreted out victims who were roughly his age and had credit cards with higher limits.
“I started taking over people’s lives,” he says. “Looking back, it seems absolutely insane.”
After botching a laptop transaction with a stolen credit card at Best Buy, he was apprehended and hit with federal charges. Facing 8.5 years in prison, DeFelippi took a plea bargain and ended up working undercover for the Secret Service for 2 years, where he helped bust numerous underground credit card fraud rings.
We sat down with DeFilippi to learn how to tackle the issue of online identity proofing from a different perspective.
Skip ahead and read the full story here:
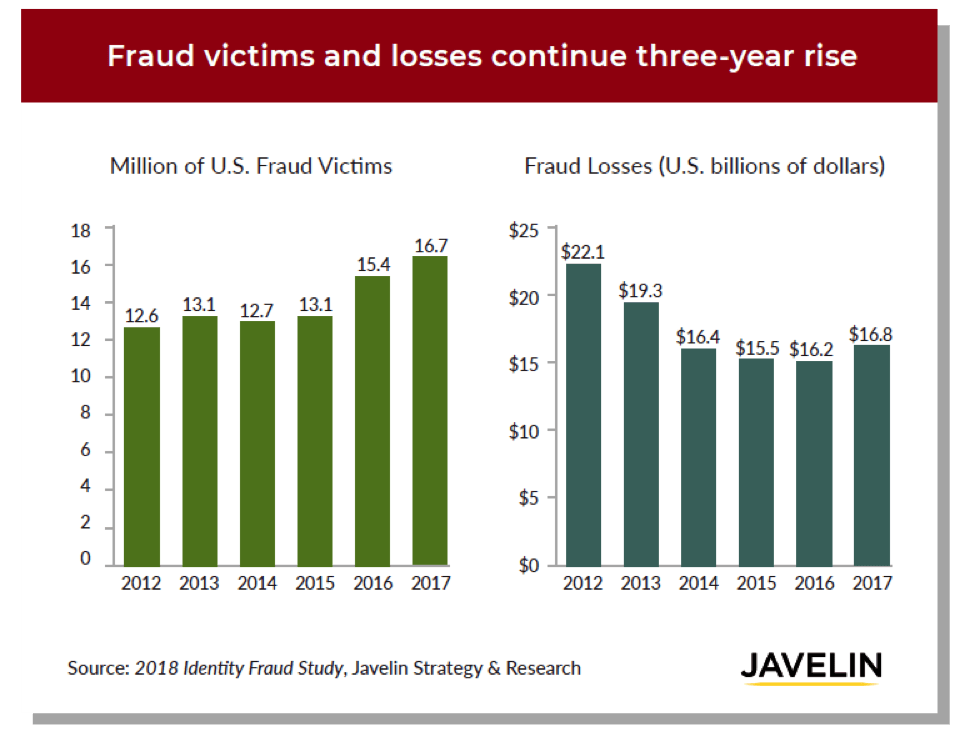
According to Javelin Strategy & Research, the last three years have witnessed an uptick in the number of fraud victims and total losses between 2015 and 2017. Since 2017 alone, this number has risen by 8%, affecting 16.7 million U.S. customers.
In tandem with rising fraud, regulatory mandates such as AML, KYC, and GDPR are placing heightened pressure on businesses to identify possible avenues to deter fraudsters and protect customers as well as the company as a whole.
Identity theft and online security has certainly evolved since the height of DeFilippi’s criminal days, but the foundations remain the same: companies with weak security systems are the low hanging fruit that cybercriminals target–both to steal ID information and to perform transactions with stolen information.
Weak customer verification = a soft target for fraudsters.
Weak customer verification methods were instrumental in DeFilippi’s success as an identity thief. The personal identifying information DeFilippi used to make online purchases and withdraw cash from victims’ bank accounts was collected from multiple sources, including forums, credit card generators, and online phishing techniques.
“For $20, you could buy full account holder information: you get someone’s online login, their name, their billing address, their card number, their PIN— everything,” DeFilippi explained. Without robust online verification methods, DeFilippi had few barriers in stealing and using the online identity of thousands.
Fortunately, there are more secure online identity verifications on market today. Unlike 2-factor authentication or knowledge-based authentication, two solutions where it is unclear whether the person transacting is the actual account owner, online identity verification allows companies to more definitively assesses an online user’s identity.
Online identity verification and the sentinel effect.
Solutions such as Jumio’s Netverify online identity verification offer two important safeguards. First, they require the user to snap a picture of a government-issued ID (e.g., a driver’s license or passport). Next, the user is required to upload a picture of themself to compare the image in the selfie with the image on the ID document. Simply by requiring a selfie, the would-be fraudster has to make the call – do I want my actual image and biometrics captured by the company I’m trying to defraud? For most fraudsters, the answer is an emphatic “no,” a powerful weapon against fraud that we refer to as the ‘sentinel effect.’
This means if a fraudster is using a stolen ID, they still have to pass the face-matching process. These more holistic solutions would prove to be a powerful disincentive (and frankly be viewed as too risky for the fraudster), who will likely move on to softer targets and systems.
Learn how to strengthen your defenses with identity proofing.
“I knew it was fraud,” DeFilippi shared. “But I couldn’t resist. The incentives were too high.”
Today, DeFilippi shares his lessons for strengthening your individual and organizational defenses against identity fraud. Hear his story first-hand and learn what it takes to protect your company and customers from the costly results of identity theft.
Read DeFlippi’s story in our free e-book here: Lessons from an ID Thief: Strengthening Your Defenses Against Customer Identity Fraud.

