Gartner® Magic Quadrant™ for Identity Verification

X


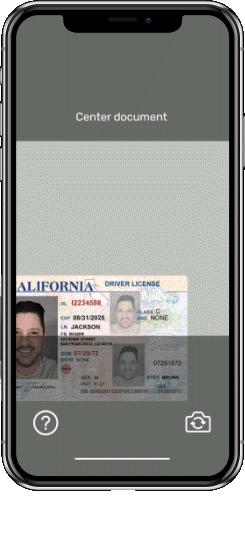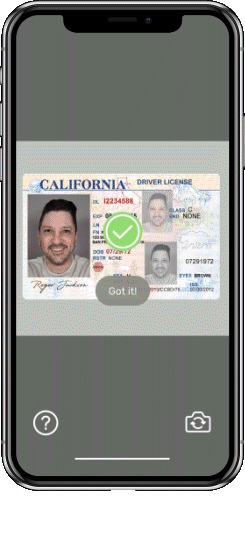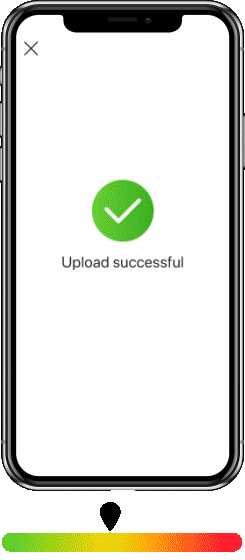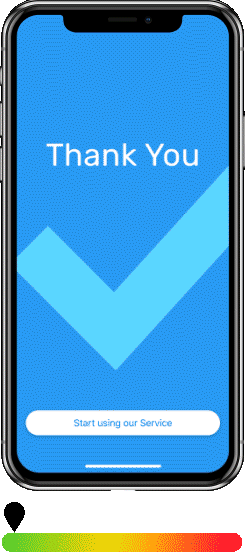

Geo IP Check
Check the risk and reputation of the user’s IP address and determine their ISP’s location. This service is especially useful for stopping the user journey before it starts if the user is attempting to hide their actual location or if their IP address has unusually high velocity that can be attributed to a bot.
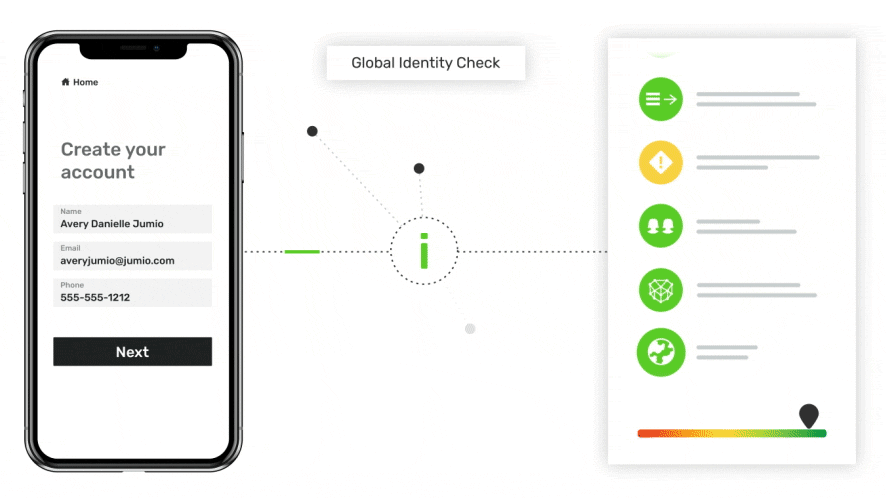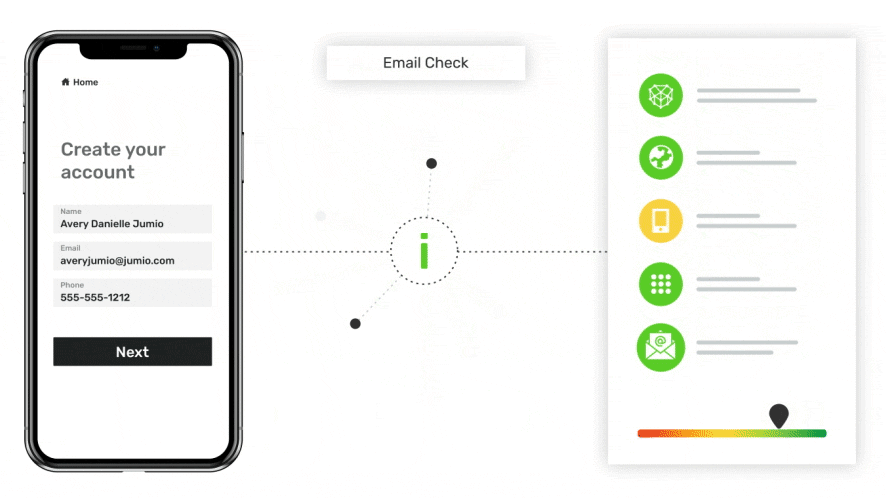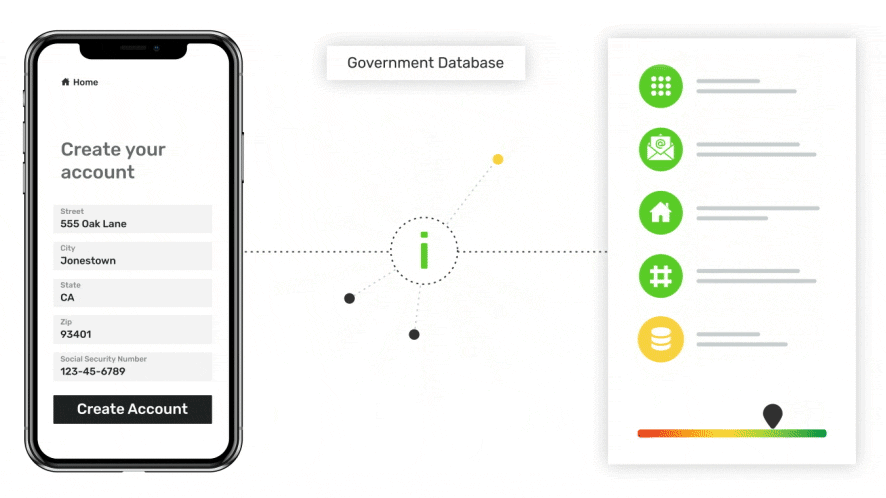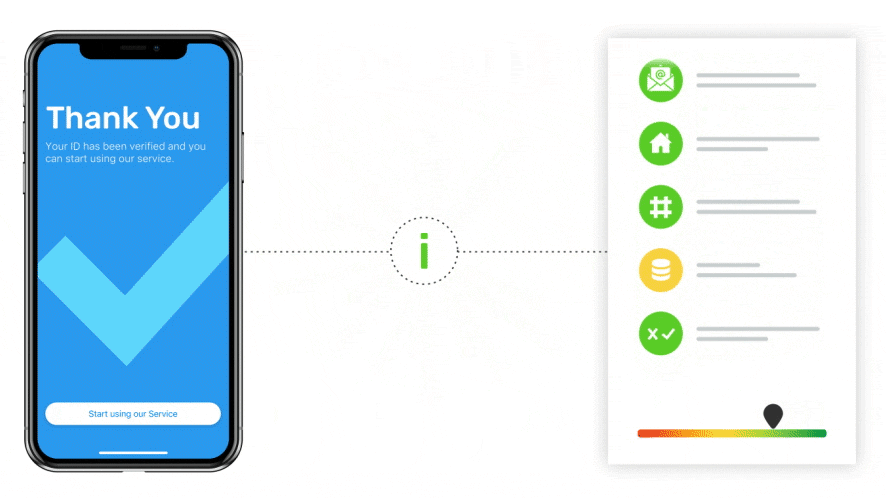
Global Identity Check
Run the user’s name, address, phone and email through a network of global identity databases to gain assurance that they belong to this person and to assess the person’s overall risk in a single, lightweight step.
Device Check
Assess the risk of the user’s device with this frictionless check. Find out if they’re using GPS emulation, device rooting or proxies to mask their location and trick your online identification flow. Examines indicators such as extensive device history, fingerprinting anomalies, usage patterns and emulators.
Phone Number Check
Determine the risk and reputation of a phone number (landlines and mobile). This service looks at usage patterns, usage velocity and phone data attributes. It also checks the number against the Global Phone Data Consortium for fraud history and evaluates messaging behavior.
Email Check
More deeply assess the risk of an email address by evaluating its velocity, age, domain details, country, fraud history and other details.
Address Checks
Validate and corroborate addresses with independent, third-party sources. Determine whether the address extracted from a government-issued ID exists in the real world, and see if the person being verified actually lives at the address on their ID.
Learn More About Address Checks
Government Database Checks
Verify that the data provided by the user or extracted from the ID card matches the data held by the jurisdiction that issued the legal document.
Learn More About Government Database Checks
Social Security Number Check
For U.S. users, verify that their name and address (and optionally their date of birth and phone number) match the Social Security number by checking databases such as the Social Security Administration, USPS, credit bureaus and other proprietary sources.
Access 500+ data sources to confirm your customers’ personally identifiable information (PII) and assess their risk.
Get a yes/no answer, automatically drive onboarding decisions and streamline your workflows.
