



Jumio helps you know and trust your customers online throughout the entire customer lifecycle. Our platform provides AI-driven services that verify the identities of new and existing users, fight fraud and help you meet compliance mandates.
Deter fraud and assess the risk of new customers in real time with identity verification and risk detection
Keep your business safe and compliant through biometric authentication and ongoing monitoring of customers
Build powerful, risk-based workflows for your exact business needs with our orchestration layer while providing a great end-user experience
One vendor. One platform. One API layer. The Jumio platform has all the solutions you need across the user journey.
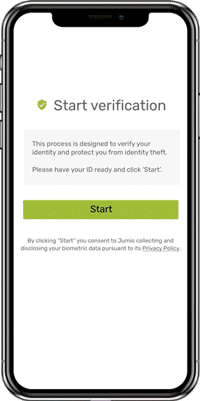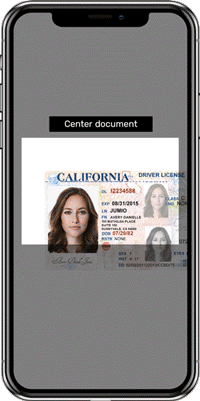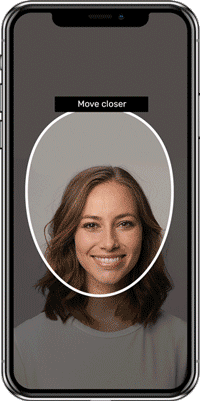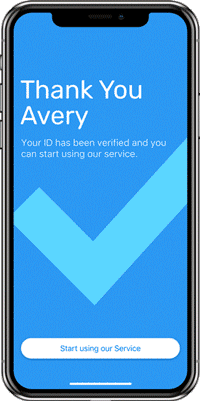
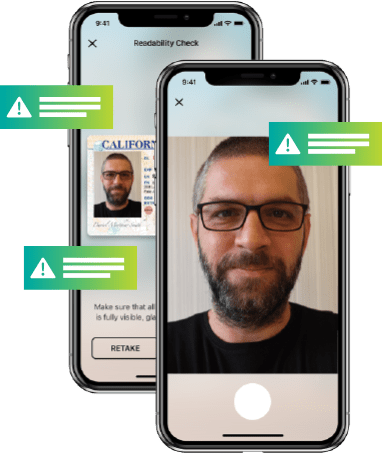

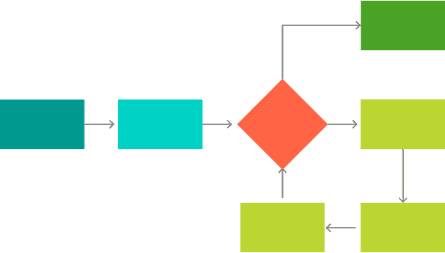
Create dynamic workflows that trigger the right checks at the right time, creating friction only for higher-risk individuals. Start with our expert-built library of over 800 rules and use the intuitive, self-service rules editor to customize them.
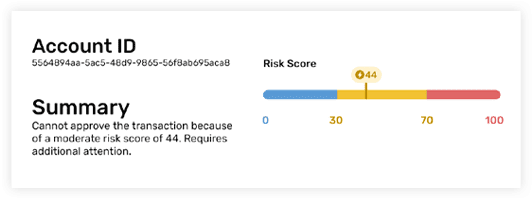
Jumio calculates a single configurable risk score from multiple risk signals to help you make the right decisions. Use the score in your workflows to trigger additional assessments as needed.
Easily spot trends in transactions, usage and success metrics from our user-friendly dashboards and run detailed reports to help you maximize efficiency.
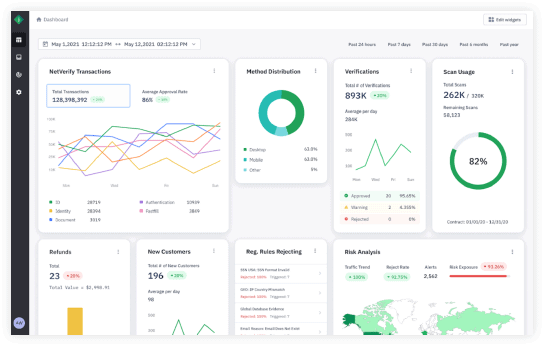




Leveraging the unmatched global coverage, scale and size of our data network, we are able to drive industry-leading, smarter machine learning and artificial intelligence to help detect and stop fraud and financial crime faster while minimizing bias and providing the highest accuracy.





