
GDPR is upon us.
The General Data Protection Regulation goes into effect this month and I have a few pretty big concerns based on some cursory conversations with my colleagues at US-based organizations.
Concern 1: Most U.S. Companies Still Unprepared for the GDPR
The first concern is their apparent ignorance just how much GDPR impacts them. GDPR isn’t just for EU businesses – GDPR applies to all companies processing or controlling the personal information of EU residents, regardless of where those firms are located.
Unfortunately, many U.S. firms may be unready or even unaware that they will likely be subject to the new EU regulations. A new survey by CompTIA found that “A full 52 percent of 400 U.S. companies surveyed are either still exploring the applicability of GDPR to their business; have determined that GDPR is not a requirement for their business; or are unsure.”
Obviously, in terms of broad-based understanding, there is a spectrum with large, established institutions who are presumably well versed in GDPR. But, on the other end, there are countless SMBs that know little about GDPR and whether it even appIies to them.
Concern 2: Understanding the Difference between Data Controllers & Data Processors
A second concern is the confusion that many organizations have with the distinction between data controllers and data processors. Given the hefty fines for non-compliance, it’s important for organizations to really understand the difference and to start asking some important questions about how your suppliers are managing and protecting the personal information of your customers.
Under the GDPR, “personal data” means information relating to an identified or identifiable natural person. This includes a wide range of personal identifiers, including name, identification number, location data or online identifier, reflecting changes in technology and the way organisations collect information about people.
- Data controllers are usually the organizations that capture and manage the personal data about their customers. Controllers determine the purposes and means of the processing of personal data.
- Data processors are often third parties used by data controllers to perform certain actions with that data. That is, processors process personal data on behalf of the controller. Companies, like Jumio, that verify the online identities of prospective new customers are considered data processors because they’re collecting personal data such as the customer’s driver’s license info and selfie, often during the account setup process, on behalf of the data controller.
Both the data controller and their data processors are bound by GDPR and both are accountable for any lapses in security.
Chapter 4, Section 1, Article 28.1 states: …the controller shall use only processors providing sufficient guarantees to implement appropriate technical and organisational measures in such a manner that processing will meet the requirements of this Regulation and ensure the protection of the rights of the data subject.
Concern 3: Not Understanding How to Properly Vet Data Processors
While you may have taken all the necessary steps to tick the GDPR compliance boxes, few organizations have thoroughly vetted their own third-parties (i.e., their data processors) to ensure they’ve take all the requisite steps to meet GDPR’s most stringent requirements – both in terms of satisfying the letter and the spirit of the law.
Often online identity verification is one of the first steps in the online account setup process and perhaps, the first point when an organization is collecting the personal information of prospective customers. This is also a process that is increasingly being farmed out to data processors like Jumio who leverage the customer’s government-issued ID (passport, driver’s license or ID card) along with a selfie to help identity proof the new user. Most of the data captured by these online service bureaus is considered personal data, so organizations need to understand how they protect their customers’ data.
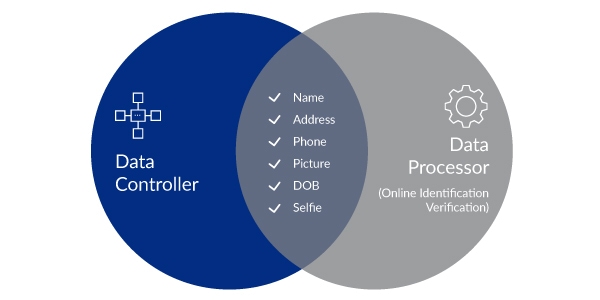
As the diagram suggests, there is usually a significant overlap between the data captured by your identity verification solution provider (often during the account setup process) and the universe of personal data captured by online businesses. That’s why we’ve developed the following list of five critical questions that organizations need to ask of their data processors – more specifically their online identity verification solution providers — to ensure they’re genuinely meeting the key GDPR security requirements.
- How is personal (PII) data encrypted and protected?
- How are verification decisions made and what recourse do data subjects have to
challenge those decisions? - Does the data process employ Compliant Machine Learning?
- Can your data retention policies be tailored to your business requirements?
- Do you have a data breach notification process in place and has it been tested?
But, how do you really know?
Unfortunately, the bar to make the claim that you’re GDPR compliant is still quite low. And many of our own customers what greater confidence that we’re truly and completely GDPR compliant. The good news for customers is that we’re already PCI DSS compliant which means that our claims about data security and data protection have already been vetted by a third party. While the GDPR is somewhat vague in terms of specifics, PCI DSS provides much better granularity.
That’s why data processors that are already PCI DSS compliant have a big head start on implementing the kinds of data security best practices and controls that the GDPR requires. Plus, PCI DSS compliant organizations have the added advantage of having their security practices, including data encryption, data retention, and data breach notification processes vetted by independent regulators.
Data controllers located in the EU and outside need to understand the pivotal role of data processors play in their own ability to stay and remain in GDPR compliance. This is especially true if you’re using an online identity verification solution given the large overlap of data captured by these identity proofing solutions. Consequently, companies need to pay special attention and fully vet their data processors to ensure that key data security and privacy provisions are in place, documented, and tested regularly.
Considering the financial, reputational, and regulatory penalties of non-compliance, it makes sense to ask a few questions and dig a little deeper.
To learn more about how Jumio can answer these questions, check out www.jumio.com/gdpr.
